How to Fix Broken sudo: Error 'sudo: /etc/sudo.conf is owned by uid 1000, should be 0'
Today, while deploying NFS, I accidentally changed the owner of all files in the /etc directory. When I tried using sudo afterward, I encountered the following error:
sudo: /etc/sudo.conf is owned by uid 1000, should be 0
sudo: /etc/sudo.conf is owned by uid 1000, should be 0
sudo: /etc/sudoers is owned by uid 1000, should be 0
sudo: no valid sudoers sources found, quitting
sudo: error initializing audit plugin sudoers_audit
The issue is that the owner and group of files like /etc/sudo.conf (and related directories) are no longer root. I searched online for solutions and tried many, but none worked—for good reason: I was stuck in a dead loop. Changing permissions with chown requires root privileges, which I couldn’t obtain. Worse, I hadn’t set a password for the root user.
I started wondering if I’d have to reinstall the system. I have so much data and configuration—it would have been a nightmare.
After rebooting multiple times, I noticed “Advanced Options” in GRUB (shown below):
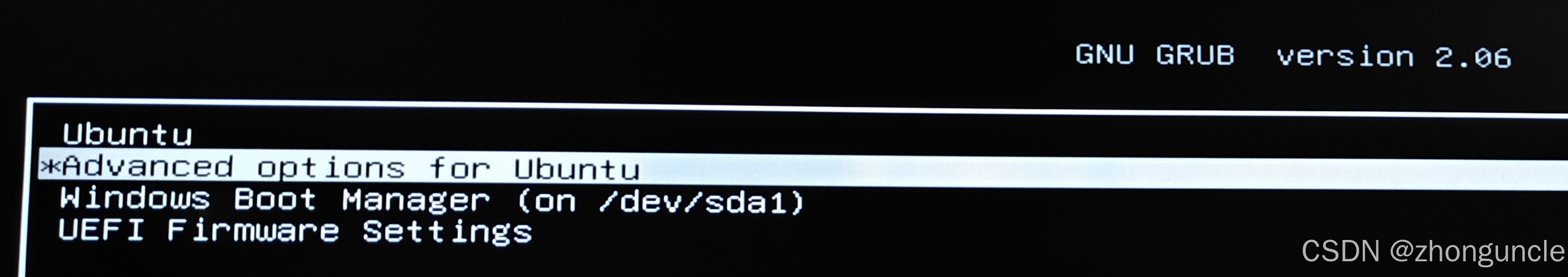
There was a “Safe Mode” option (shown below). I figured I’d try it as a last resort:
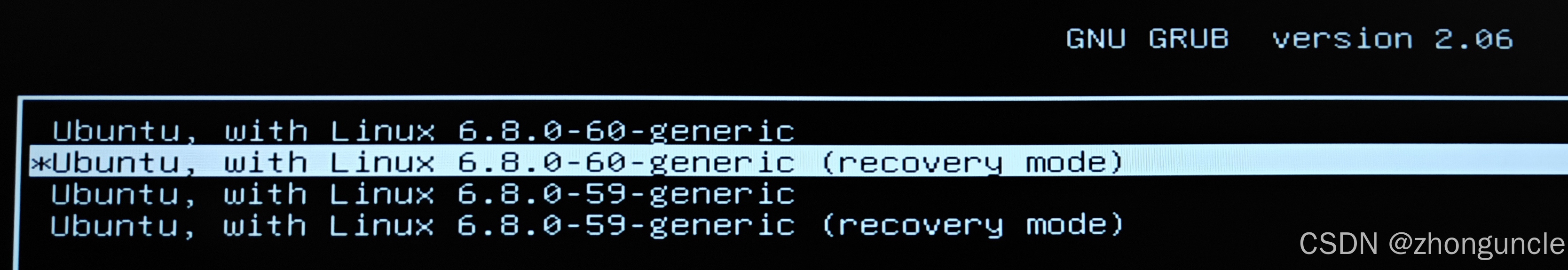
This mode is essentially a command-line interface with extremely high privileges. In Safe Mode, you can use chown to restore the correct root ownership to the files you mistakenly modified. After that, sudo will work normally again.
Whether to use
1000:1000orroot:rootdepends on your specific system setup.
I hope these will help someone in need~